
Home › Archives for May 2017

SEO (Search Engine Optimization) and it's types
Hello Guys Today i will tell you little bit about SEO but first: What is SEO? SEO is stands for Search Engine Optimization and it's ...

How to protect from ransomware CryptoLocker (Wanna Cry) - Part 2
Hi guys here is part 2 of How to protect from ransomware CryptoLocker so here is list which was remaining: 6.Disconnect your computer: ...

How to card Nike store - Latest carding method
Today let me show how to card Nike Store What You Need: - RDP (if you can't buy RDP, it's works with PREMIUM Socks5 - Tested and ...
How to get WIFI passwords of your city using mobile
Hello everyone i find android app which can show you wifi passwords of your city by allowing the GPS (for detecting location) Here Hope ...

How to protect from ransomware CryptoLocker - Part 1
Hello guys let's do our best to protect ourself from randsomware maybe i don't need to explain about " randsomware " it ...

How to get WIFI passwords of your city using mobile
Hello everyone i find android app which can show you wifi passwords of your city by allowing the GPS (for detecting location) Here Hope ...
Check It out My Website i've coded
Hello Guys long time no see coz i was pretty busy at my exams and after that i've to code my website. Wanna check? Here . I'm no...
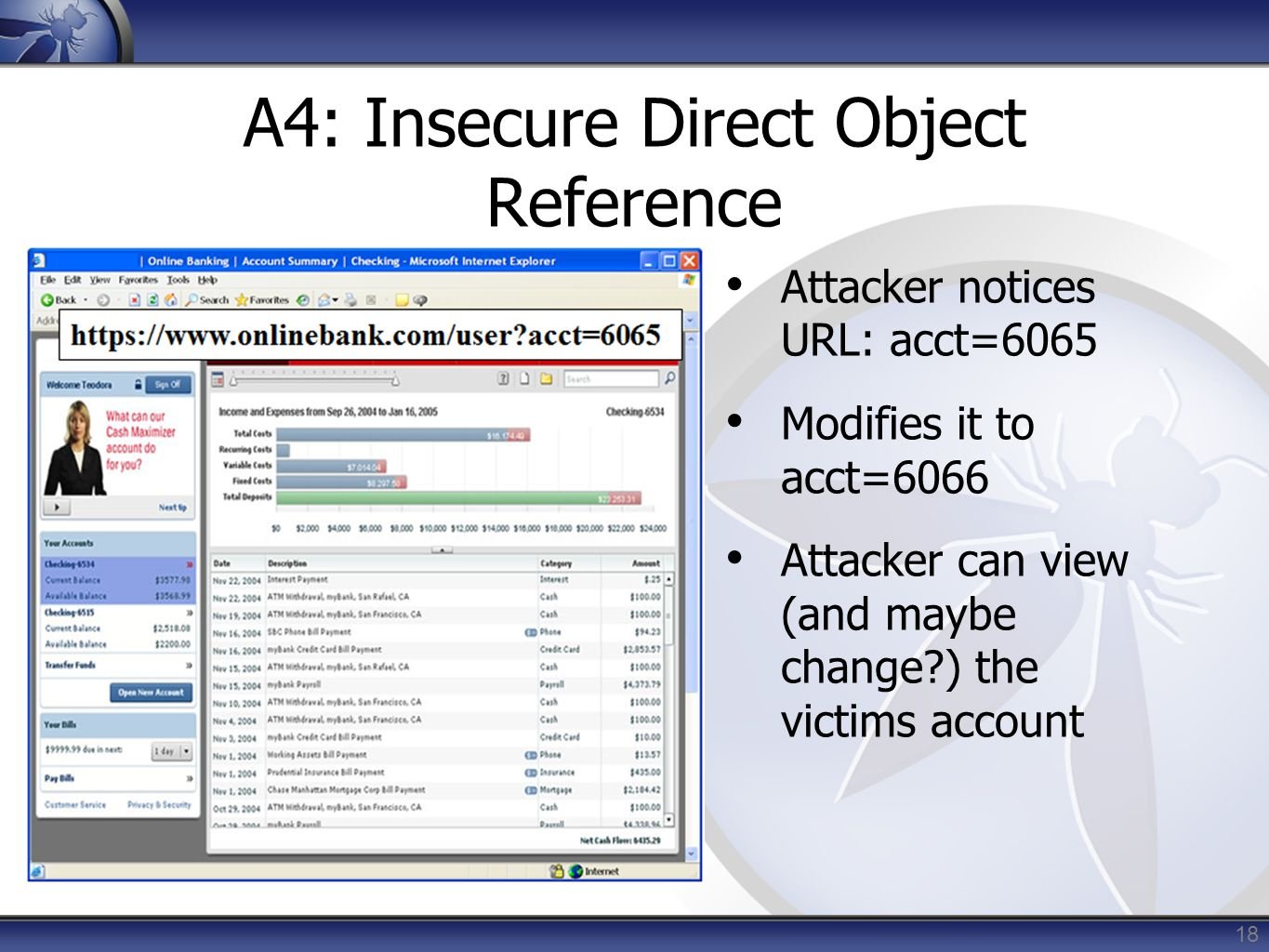
Insecure Direct Object References
Insecure Direct Object References: According to owasp : Insecure Direct Object References occur when an application provides direct a...
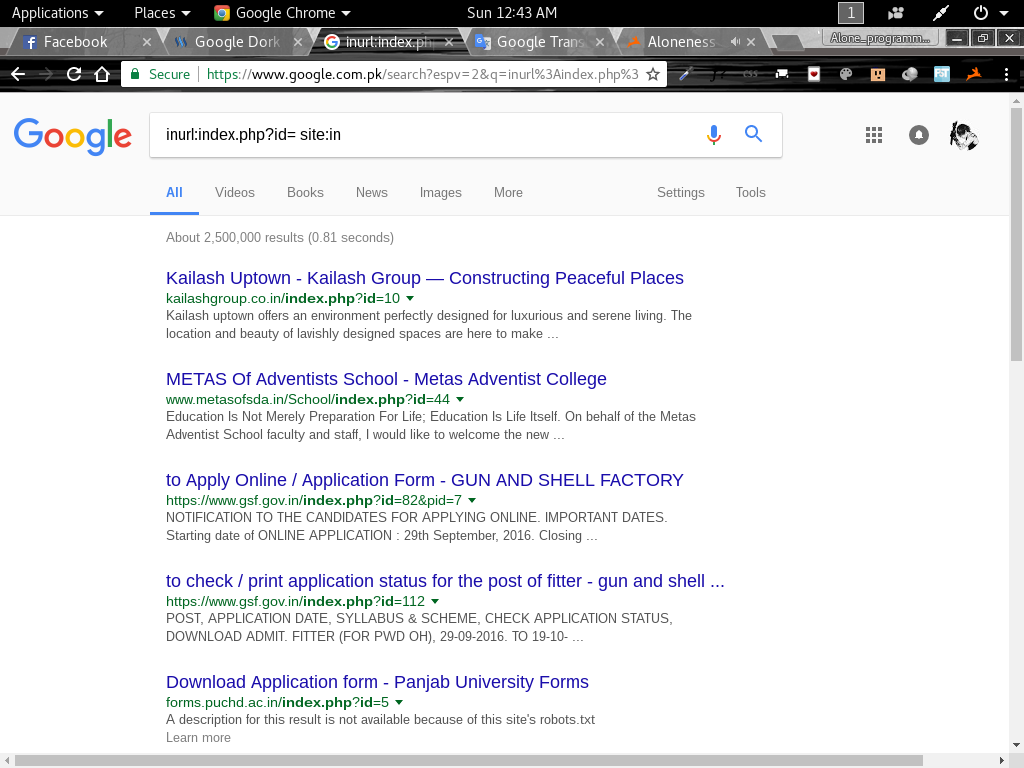
Google Dork (SQLI) To Find Vulnerable Websites For Hacking
Google Dork (SQLI) To Find Vulnerable Websites for Hacking Hello guys today i will show you how we can get websites for hacking :) Simp...
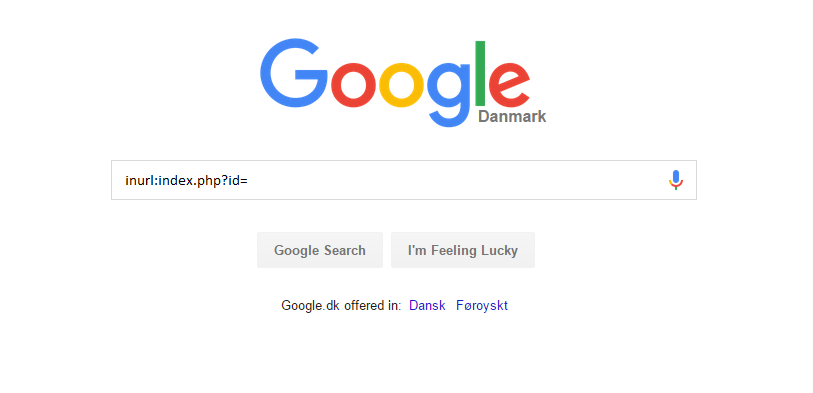
Google Dorks (Google Database Hacking)
Google Dorks (Google Database Hacking) A Google dork query, sometimes just referred to as a dork, is a search string that uses advance...
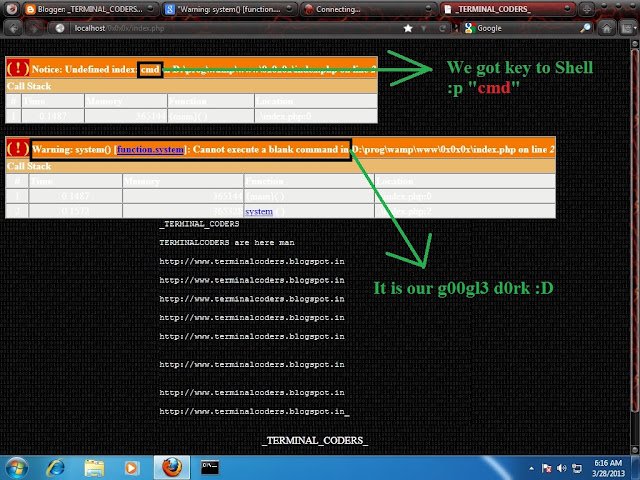
RCE (Remote Code Execution)
Another Name of RCE is also called arbitrary code execution .Which is used to describe an attacker's ability to execute any command of ...

Facebook Phishing Page (Method to hack Facebook account)
Facebook Phishing Page - Method to hack Facebook account: Phishing is the attempt to obtain sensitive information such as usernames, p...

Cross-Site Request Forgery (CSRF)
Today i will explain another way of how hackers hack people accounts but first let's what is CSRF ? Cross - Site Request Forgery ( ...

Broken Authentication and Session Management (Most Common Vulnerabilities to Hack Websites)
Today i will told you about one of the most common Vulnerability to Hack websites .But first let me told you THIS IS JUST FOR EDUCATION ...
What is XSS (Website vulnerability)
What is XSS (Cross Site Scripting) Cross-site scripting (XSS) is an injection attack which is carried out on Web applications that acce...

What is SQL INJECTION (Website vulnerability)
What is SQL INJECTION An attack technique used to exploit web sites by altering backend SQL statements through manipulating application i...
How did Websites get hacked?
Today i'm gonna told you about how did hackers hack websites. Hackers acually found a bug (vulnerability) (Like SQL Injection,XSS,RCE)...

Hackers Type: Gray Hat Hackers (Both White and Black Hackers)
They are both White and Black hat hackers.Gray Hat hackers don’t steal money or information (although, sometimes they deface a website or t...

Hackers Type: Black Hat (Crackers)
They are also known as crackers, these are the men and women you hear about in the news. They find banks or other companies with weak secur...

Hackers Type: White Hat (Ethical Hackers)
White Hat hackers are also known as Ethical Hackers. White Hat hackers are the good guys of the hacker world. They’ll help you remove a vi...
Cracking WebSites Login Password (Authorizations)
Salam! Everyone, today we will take a look at How Crackers able to crack the auth System of Websites. Maybe you don't notice i...
Subscribe to:
Comments (Atom)






















